Recent mass shootings in Christchurch, Poway, and El Paso, as well as the lesser-known attack on a synagogue in Halle, Germany all have something in common other than being acts of violence. The perpetrators all had an online presence on a forum known as "8chan".
After the El Paso attack, 8chan was dropped by service providers and went offline. The shooter in Halle couldn't announce the attack on the forum; however, it was still live-streamed, similar to the attack in Christchurch. The attacker also used the name "anon", short for anonymous, a typical username used for privacy in forums such as 8chan.
8Chan has since rebranded as "8kun" and is back online as of November 3rd, 2019. The screenshot below shows 8kun's landing page in TOR.
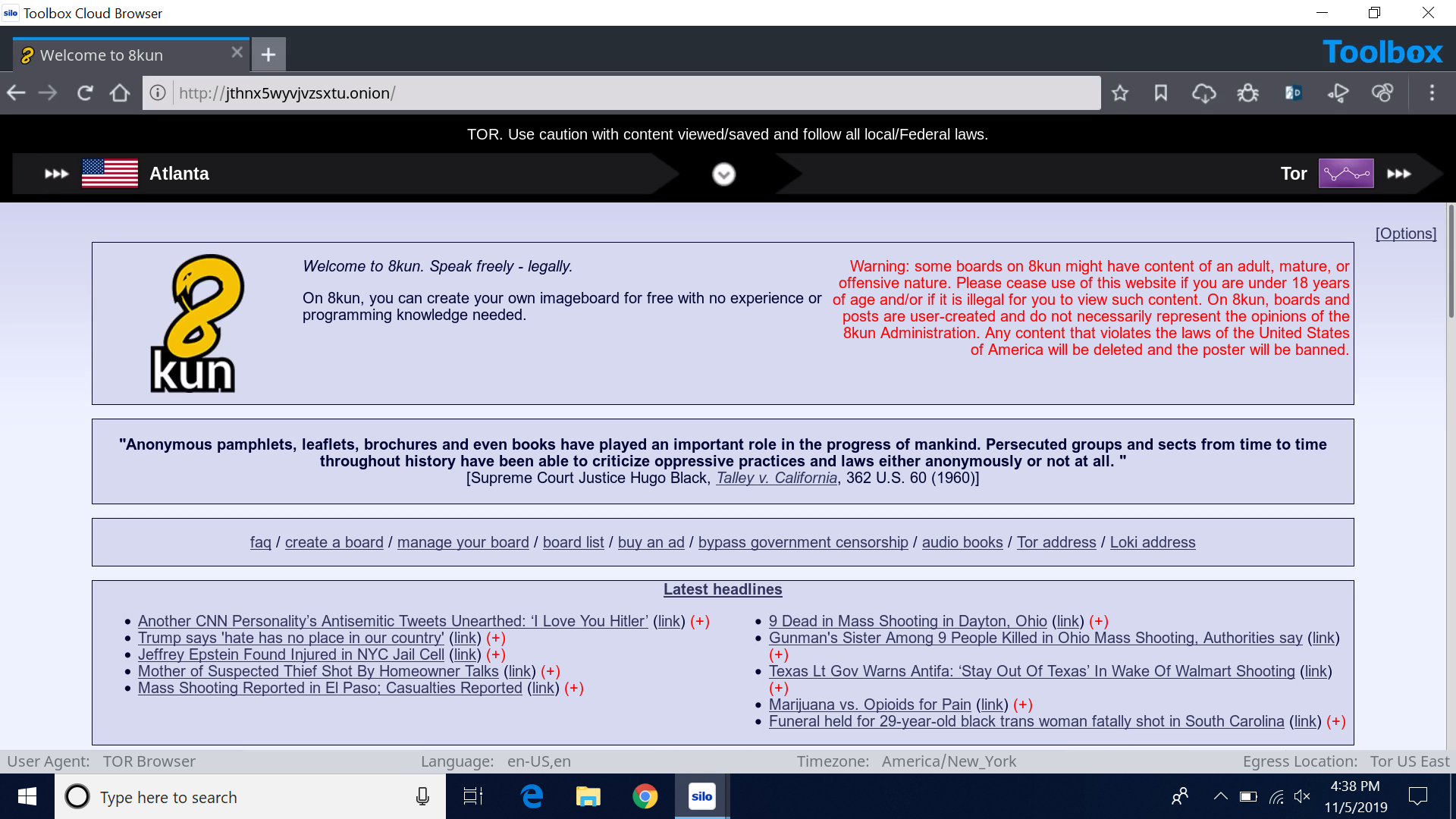
Forums such as 8kun are not only a gathering place for users to gain inspiration to commit attacks. They also serve as dissemination points for manifestos furthering the spread of this type of terrorism.
The Christchurch shooter's manifesto was posted on 8kun's predecessor, 8chan. The manifesto was also taken from the site, printed, and can be purchased physically in Ukraine.
Other acts of violence inspired on such forums originated from the "Qanon" conspiracy. A user known as "Q" made posts developing a cult-like following, even inspiring a standoff with law enforcement at the Hoover Dam and other non-lethal attacks.
In August of 2019, the FBI stated that conspiracy theories like Qanon encourage "the targeting of specific people, places, and organizations, thereby increasing the risk of extremist violence against such targets."
Navigating TOR or other non-standard networks may be difficult for organizations to accommodate. In some cases, accessing TOR violates organizational policy. In others, the organization lacks the necessary infrastructure. Whatever the reason - not monitoring forums such as 8kun causes a critical intelligence gap.
The trend of terrorism migrating into hidden forums with "anonymous" users is not slowing down. The 8kun launch in TOR may well increase site activity due to the nature of TOR's inherent security.
To TOR or not to TOR? Given this new wave of cyber-inspired terrorism, the answer is most definitely to TOR.
For more information, visit this page or contact us at osint@authentic8.com